Secure Your Software Supply Chain with Managed Dependency-Track

What is Dependency-Track?
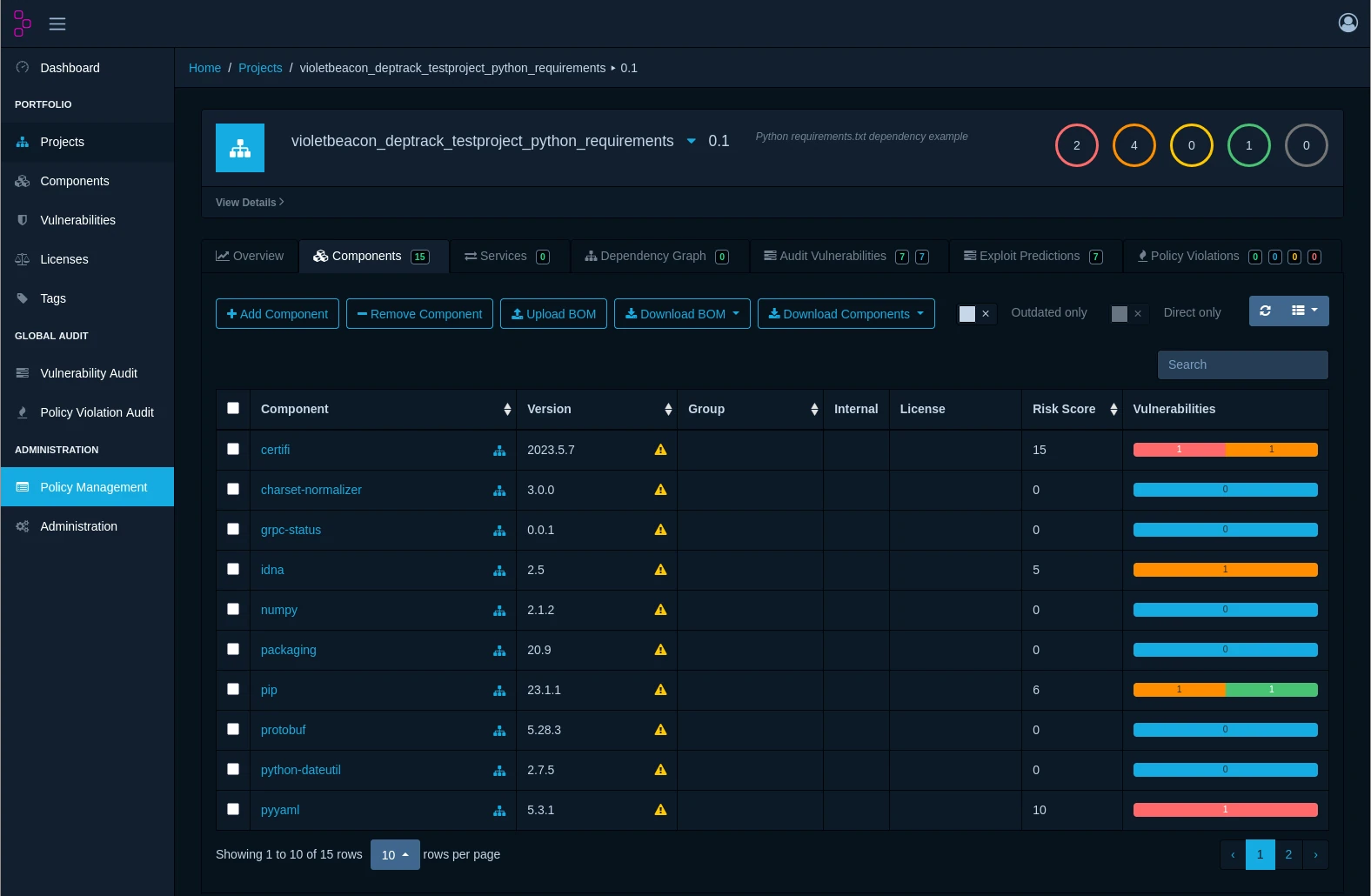
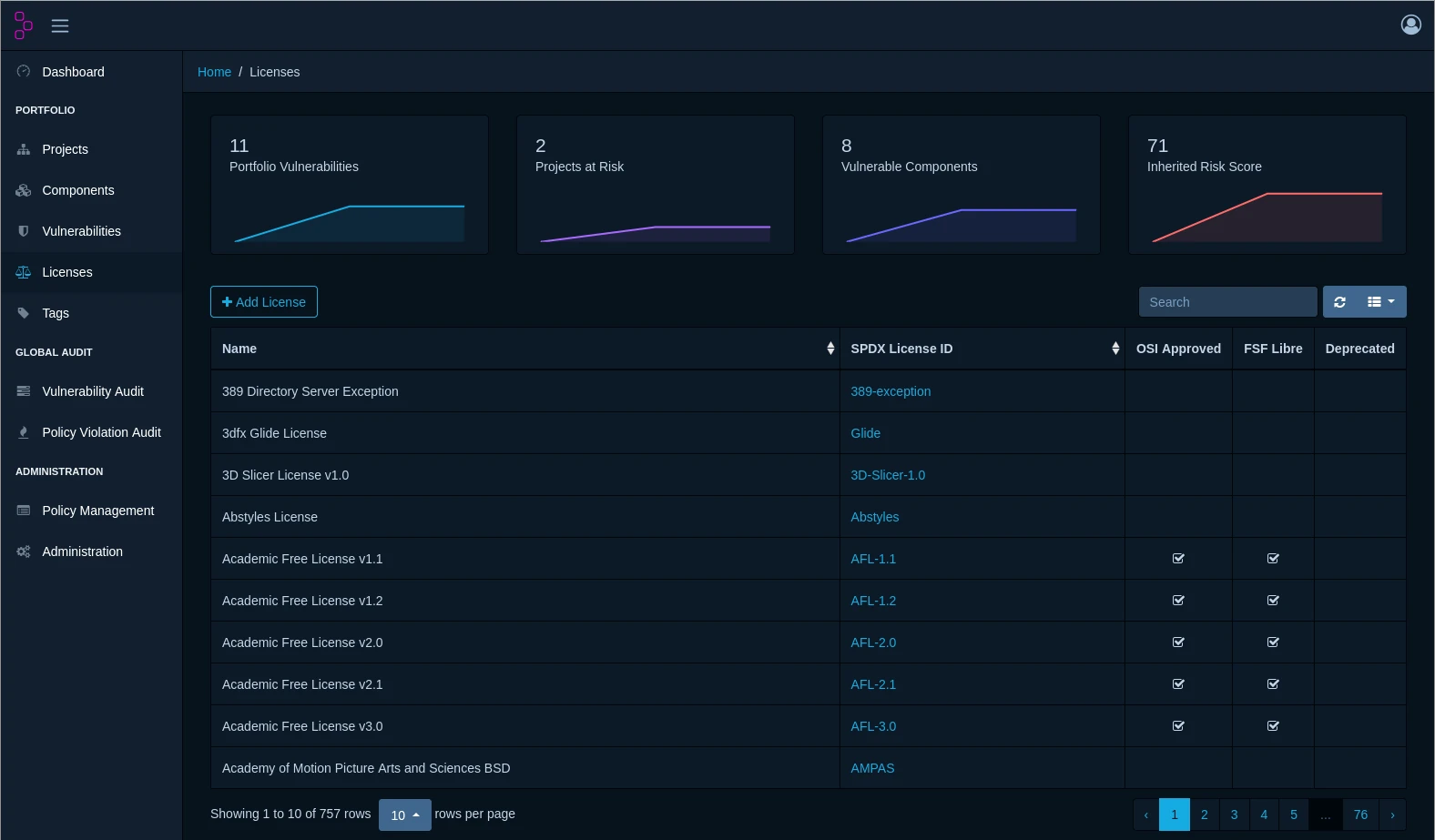
Dependency-Track is a powerful, open-source Software Composition Analysis (SCA) platform that provides comprehensive visibility into your software supply chain risks. It continuously monitors your applications' dependencies, identifies vulnerabilities, and helps you maintain secure, compliant software throughout your development lifecycle.

Why Your Organization Needs Dependency-Track
Modern applications rely on hundreds or thousands of third-party components and libraries. Each dependency represents a potential security risk that could expose your organization to data breaches, compliance violations, and operational disruptions. Dependency-Track gives you the information you need to make informed decisions about your software components.
Key Benefits of Our Managed Dependency-Track Service
Complete Supply Chain Visibility
Get a comprehensive inventory of all components across your entire application portfolio. Track direct and transitive dependencies, understand component relationships, and maintain accurate bills of materials (BOMs) for every application.
Real-Time Vulnerability Monitoring
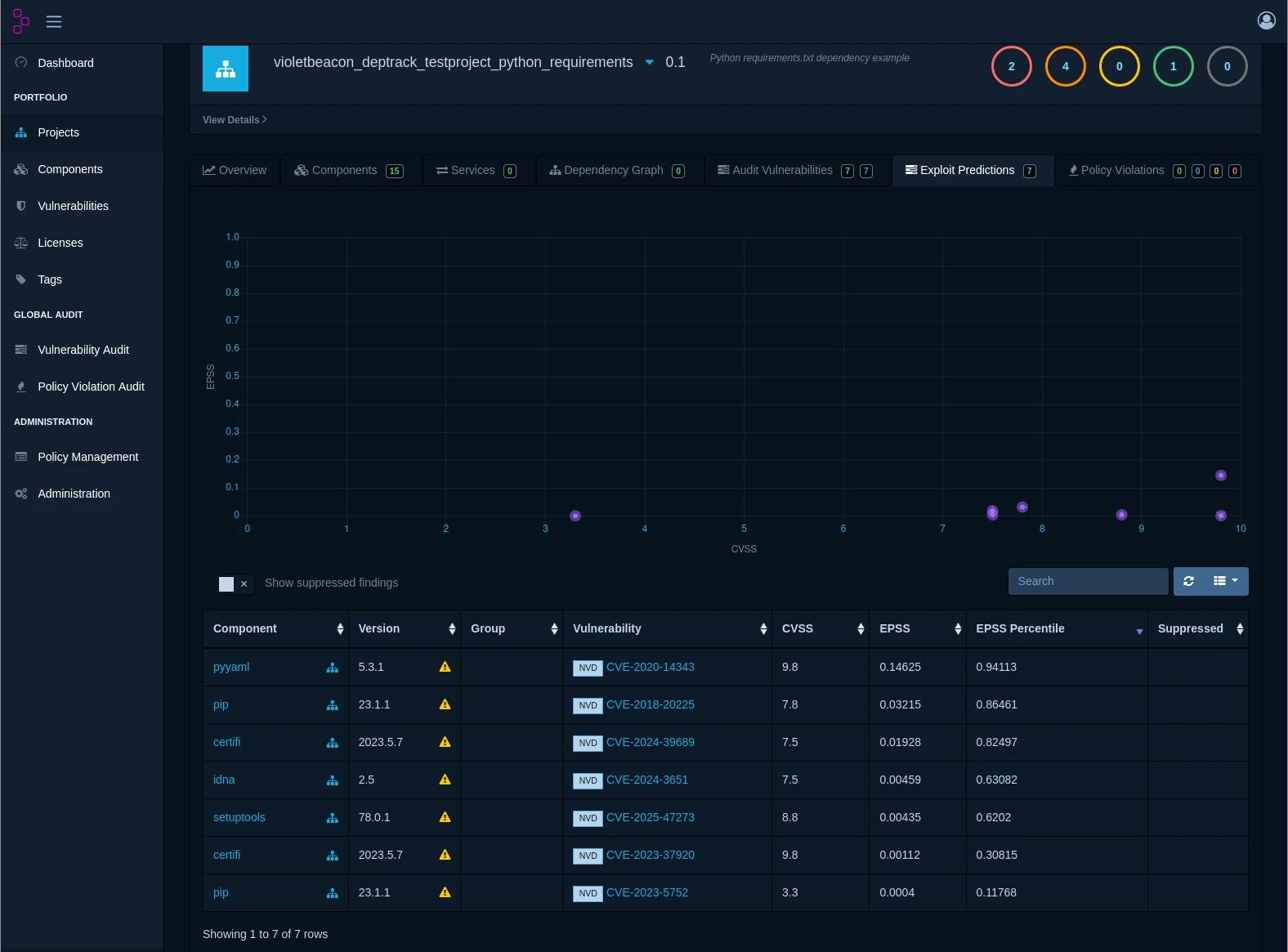
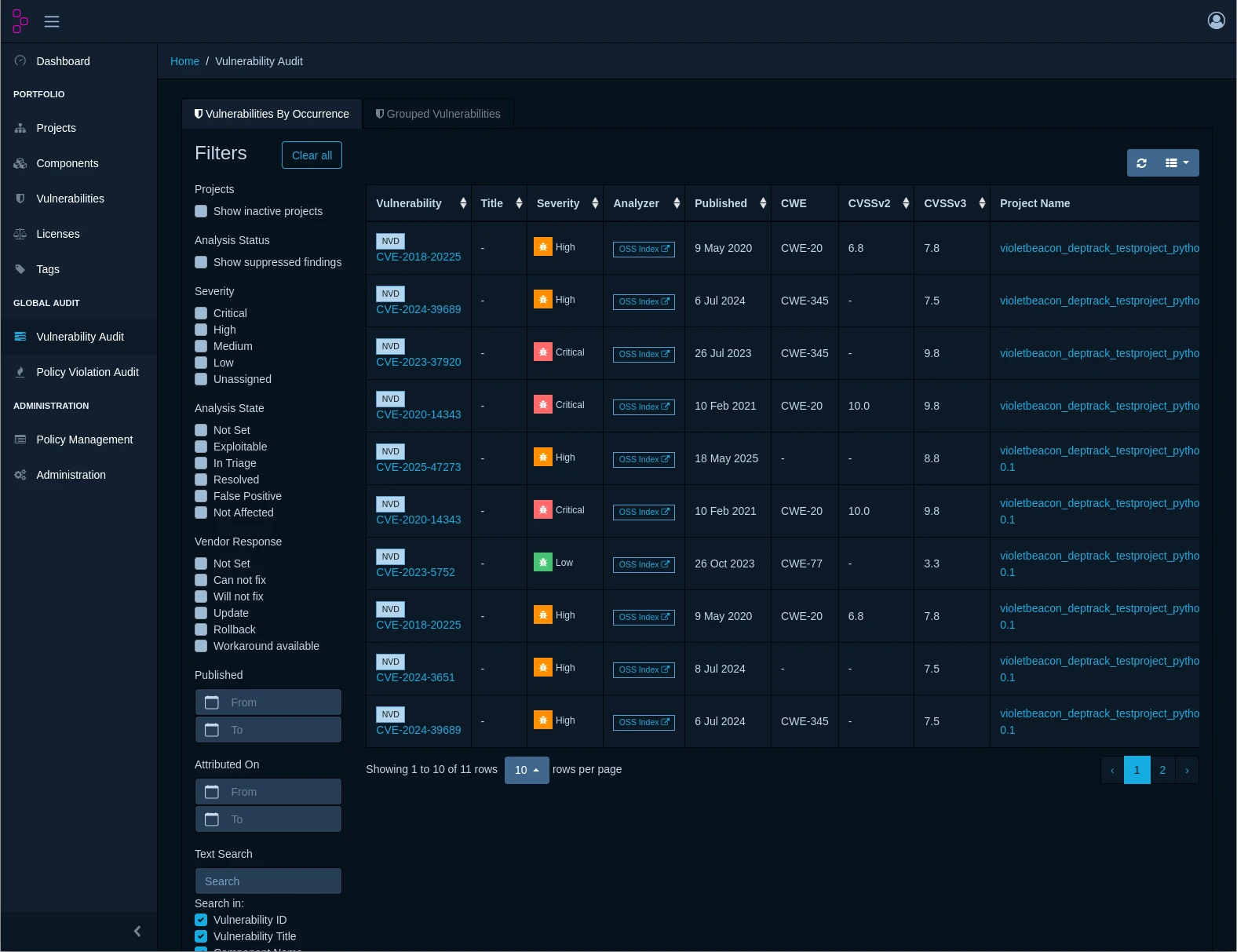
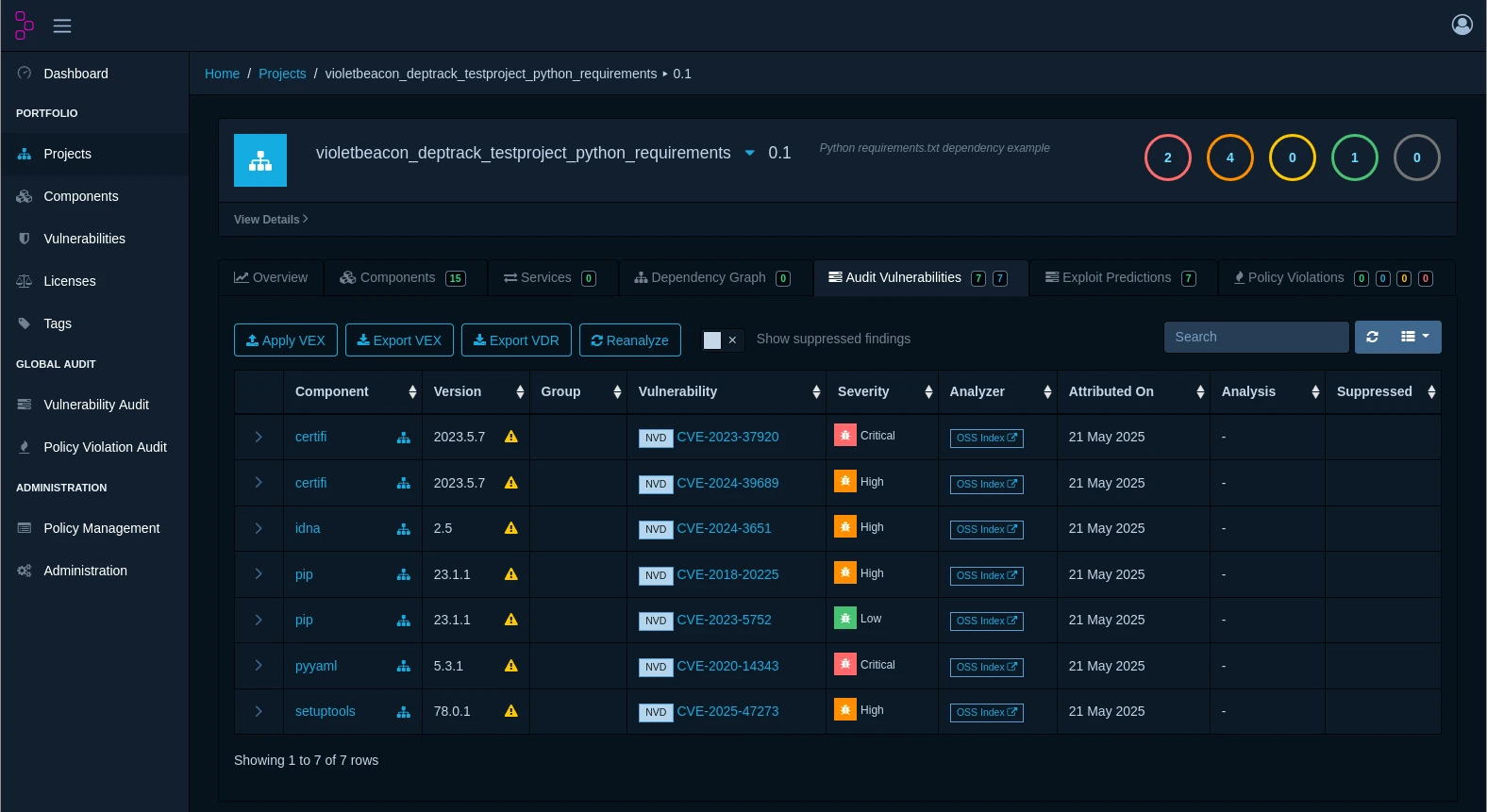
Stay ahead of emerging threats with continuous vulnerability scanning against multiple intelligence sources including the National Vulnerability Database (NVD), GitHub Security Advisories, and VulnDB. Receive instant alerts when new vulnerabilities affect your components.
Risk-Based Prioritization
Not all vulnerabilities are created equal. Our platform helps you focus on what matters most by providing risk scores, exploitability metrics, and business context to prioritize remediation efforts effectively.
Compliance Made Simple
Meet regulatory requirements and industry standards with automated compliance reporting. Generate detailed audit trails, track remediation progress, and demonstrate due diligence to auditors and stakeholders.
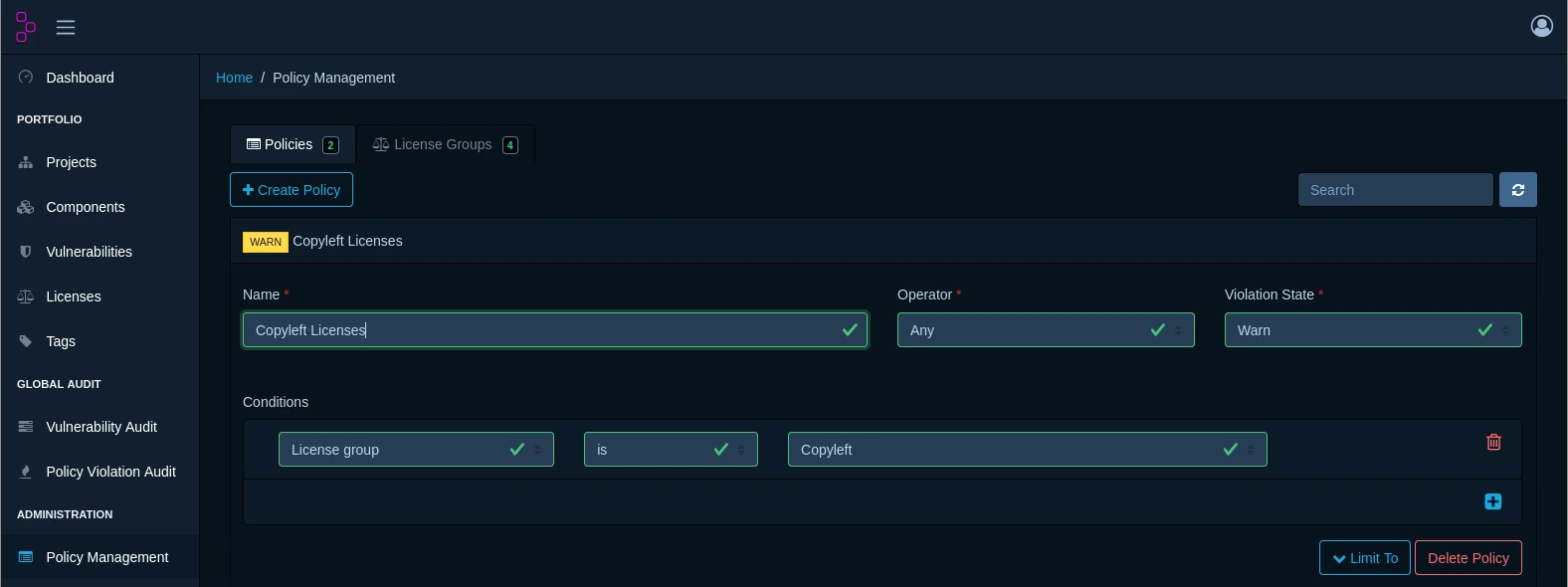
Policy Enforcement
Implement automated policies that prevent risky components from entering your applications. Set rules based on vulnerability severity, license compatibility, component age, or custom criteria that align with your organization's risk tolerance.
License Risk Management
Avoid costly legal issues by tracking and managing open-source licenses across your software portfolio. Identify license conflicts, ensure compliance with usage terms, and make informed decisions about component adoption.
SSO-Ready At No Additional Cost
Dependency-Track supports any SSO provider that supports OpenID Connect, including Microsoft Entra/Azure AD, Google, Auth0, Gitlab, OneLogin, Keycloak, etc.
No Vendor Lock-in
Dependency-Track is Free Open Source (FOSS) software licensed by the Open Worldwide Application Security Project (OWASP) under Apache License version 2.0. Want to bring your Dependency-Track installation in-house? You can set up a new instance, generate an export from the VioletBeacon managed instance and migrate the data to your in-house instance.
VioletBeacon Added Features
We are continually adding new features and improvements. Improvements to Dependency-Track are submitted to the upstream project. Some features, such as the VioletBeacon managed BOM build environments and BOM generation speedups, are kept proprietary.
Custom Improvements
VioletBeacon is available for contracted improvements to your Dependency-Track instance.
Why Choose VioletBeacon's Managed Dependency-Track Service?
Zero Infrastructure Overhead
We handle all the complex setup, configuration, and maintenance so your team can focus on what they do best—building great software. No need to provision servers, manage databases, or worry about scaling.
Expert Configuration & Optimization
Our security experts configure Dependency-Track specifically for your environment, ensuring optimal performance and accurate results from day one. We fine-tune policies, integrations, and workflows to match your development processes.
24/7 Monitoring & Support
Your security can't wait for business hours. We provide round-the-clock monitoring, maintenance, and expert support to ensure your Dependency-Track instance is always available and performing optimally.
Seamless Integration
We integrate Dependency-Track with your existing CI/CD pipelines, security tools, and development workflows. Support for popular platforms including Jenkins, GitLab, GitHub Actions, Jira, and Slack ensures smooth adoption across your organization.
Enterprise-Grade Security
Your data is protected with enterprise-grade security measures including encryption at rest and in transit, regular security updates, backup and disaster recovery, and compliance with industry security standards.
Scalable & Reliable
Our managed platform grows with your needs. Whether you're a startup with a few applications or an enterprise with thousands of components, we provide the reliability and scalability you require.
Supported Languages















How it Works

Manual Mode
- Build the CycloneDX file locally
- Upload the CycloneDX file to Dependency-Track web interface or via the API
- Review the report in the web interface or via the API

CI/CD Integration Mode
- Build CycloneDX file locally or trigger a repo pull via the API. Integrations are available for Jenkins, GitHub and GitLab. (If a repo pull is triggered, VioletBeacon will build the CycloneDX file itself.)
- Dependency-Track analyses the dependencies
- Results are available via the API and builds are blocked if vulnerabilities are detected. The pass-failure criteria and actions are configurable.

Repo Push Mode
- VioletBeacon monitors repositories and pulls changes when a change is detected.
- VioletBeacon analyses the project and builds the CycloneDX file
- CycloneDX file is pushed to Dependency-Track
- Results are available via the API or web interface
Pricing
| Standard Dedicated Server | USD $175/month |
|---|---|
| Large-1 Dedicated Server | USD $280/month |
| Large-2 Dedicated Server | USD $560/month |
| Custom | Contact us for specifications and a quote |
Get Started Today
Gain control of your software supply chain security. Our managed Dependency-Track service gives you the visibility, intelligence, and control you need to build secure software with confidence.